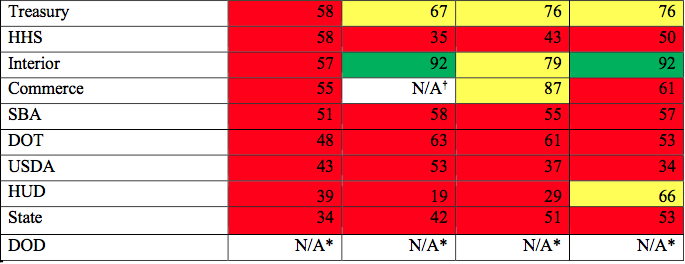
From: Federal Times
***
Under the current policy, established 15 years ago, agencies are required to review security controls every three years. Modern best practices call for continuous monitoring of systems, using automation tools like those offered through the Continuous Diagnostics and Mitigation (CDM) program.
Without the update, “Circular A-130 remains an obstacle to the full adoption of this modern, automated approach to cybersecurity across government,” the senators wrote.