From: Network World
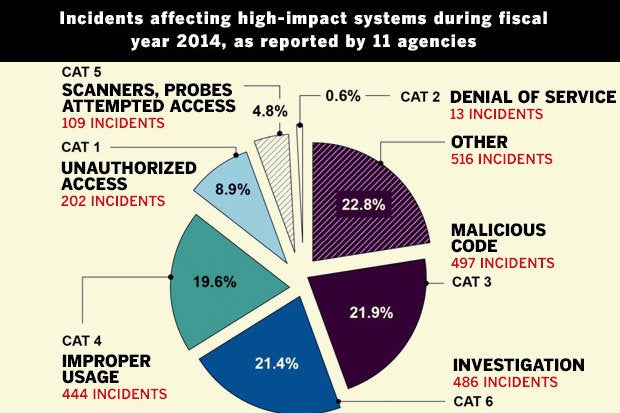
GAO: The loss of high impact” systems could cause individuals, the government, or the nation catastrophic harm
***
An underlying reason for these weaknesses is that the agencies had not fully implemented elements of their information security programs. For example, security plans did not always address controls specific to high-impact systems, those with significant security responsibilities did not always complete specialized training, systems ‘assessments were not comprehensive, and continuous monitoring strategies were incomplete.”
***