From: SecurityWeek
By Identifying Areas of High Risk Across the Entire Infrastructure, Countermeasures Can be Implemented Where They’re Needed Most.
By Eric Knapp
There’s been a lot of discussion around SCADA and ICS cyber security—it impacts our critical infrastructures, which drive a number of key resources including energy, fuel, clean water, biotech and more. What’s more, it drives revenue, and so there’s been a mad rush to the well, a throng of enterprise technology vendors eager to drink deep from this new and lucrative market. Unfortunately, traditional cyber security models don’t always apply, and so the water’s getting muddy but nobody’s thirst is being slaked.
The problem lies in the complexities of our critical infrastructures and the many highly specialized embedded systems that comprise them. Because they’re specialized, traditional tools don’t always fit, and because they’re largely purpose built using embedded run time operating systems, man of those tools simply can’t accommodate them. We’ve all heard about the inherent vulnerabilities of SCADA and ICS systems, yet we continue to focus cyber security on the surrounding IT systems using these traditional IT tools. The solution requires a new security model that addresses the specific challenges of the industrial automated world.
The first step is to consider all of the areas that need to be addressed. There are “traditional” IT networks with “traditional” security concerns and countermeasures, but there are also SCADA network zones, and then also the automated process/device networks. These three networks have unique security challenges, and different requirements for countermeasures. The devices and assets used in each zone are different, the networks are different, and the data being produced and/or utilized by each are different. The failure of most cyber security efforts to date has been caused by a simple misunderstanding that cyber security is purely an IT effort, and that to apply cyber security to a control environment means to identify and secure those recognizable elements—Ethernet, TCP/IP, Windows, et al.—using traditional cyber security countermeasures such as Firewalls and Anti Virus software. The unique aspects of the SCADA systems and the device networks are ignored completely, hence the infrastructure is left with several highly vulnerable attack vectors.
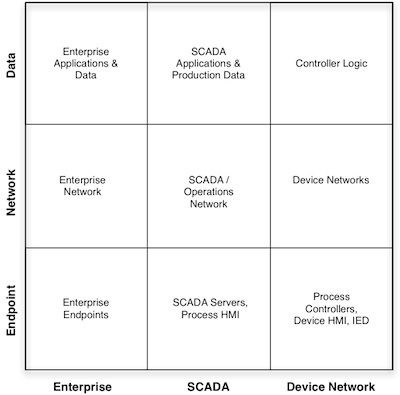
If you visualize all three environments as a 3×3 matrix—three levels of security in each of three zones—these differences become more obvious.
Looking at the quick diagram (right), we see nine unique security challenges. Reading the bottom row left to right, the endpoints shift from modern computing systems used in the enterprise, to legacy Windows platforms (which are probably unpatched due to 100% uptime requirements), to purpose built embedded devices. The “network” row shifts from modern and dynamic high-speed Ethernet networks, remote applications, and cloud services, to very rigid Ethernet systems communicating via TCP/IP and real-time industrial protocols, to the device network which consists of industrial fieldbus protocols (some of which are running over a real-time Ethernet protocol such as IEC 61850 or Ethernet/IP, some of which are still using serial or coax control buses). The “data” column shifts drastically from the latest trends in the enterprise—ultra-connected applications such as SaaS, Cloud and social media—to the highly controlled SCADA systems—control logic SDKs, SCADA servers, Historians—to the purely logic driven control programs enforced by distributed controllers throughout the device network.
Why is this important? Because it helps to clarify the pond, helping to separate the often overzealous claims of the vendor community by placing product and technology claims into a larger context. It exemplifies the inadequacies of an incomplete cyber security deployment. We’ve all heard statements—or maybe even said them ourselves—such as “We’re safe from Stuxnet because we’ve caulked our USB interfaces,” or “We’re safe because we put a firewall in place at the edge of the SCADA network.” These are all great measures, but each only addresses a single square in the nine square matrix, leaving the rest unguarded (and the matrix is highly simplified as it is, representing only a fraction of the diversity and complexity of a typical industrial environment). How do you secure the PLC from executing bad logic? How do protect the device network from injected protocol attacks? How do you protect an infrequently patched SCADA server from almost daily doses of new malware?
In my next column, I’ll start answering those questions by mapping available countermeasures to the 3×3 security model. But be warned: there are weak areas and even gaps in current control architectures that can’t be easily addressed. However, by identifying those areas of high risk and vulnerability across the entire infrastructure, those countermeasures that are available today can be implemented where they’re needed most, for maximum effect. Your entire company—from the corporate network, to the SCADA systems to the automated device networks—will be more safe, reliable and secure because of it.
Leave a Reply